Container images are software time capsules. Intentionally immutable by design, they will not get security updates automatically. Doing this task that is crucial to security is up to you. However, rebuilding and redeploying applications to pull in updates comes with the risk that any software update does, and requires testing to ensure that no downtime will occur.
Rebuilding and redeploying is potentially disruptive, but also the only remedy to a vulnerable image.
Scanning images for known vulnerabilities informs the administrator or DevOps engineer when such a procedure is needed.
In this article, we describe what container vulnerability scanning is, how it is done, and how open source tools help automate the procedure.
What is vulnerability management and what does Harbor have to do with it?
Vulnerability management relates to how we handle vulnerabilities in our systems. It can be broken down into the following steps:
- Identification
- Evaluation or assessment
- Mitigation
The first step is to be aware that there is a problem. The second is to evaluate how critical the problem is. Finally, the third is to actually do something about it. There is actually also a fourth step: to report vulnerabilities you have found, in particular if your users have been affected by it. That is a non-technical step, though, so we focus on the first three.
When it comes to containerized applications, there are two kinds of vulnerability management processes we need to consider. The first is static analysis of the container images we have in our system. Are they vulnerable? The second is to investigate our applications while they are deployed, to see if they behave in a way that may be the result of an attack. This article focuses on the first kind, and an upcoming one on the second.
Static analysis of container images, before they are deployed, requires a way to work with container images as they are stored. Container images are stored in container registries. Harbor is such a container registry. A container registry is a system where you can store your container images in order to later use the images when you deploy your application (e.g. as a Pod in a Kubernetes cluster).
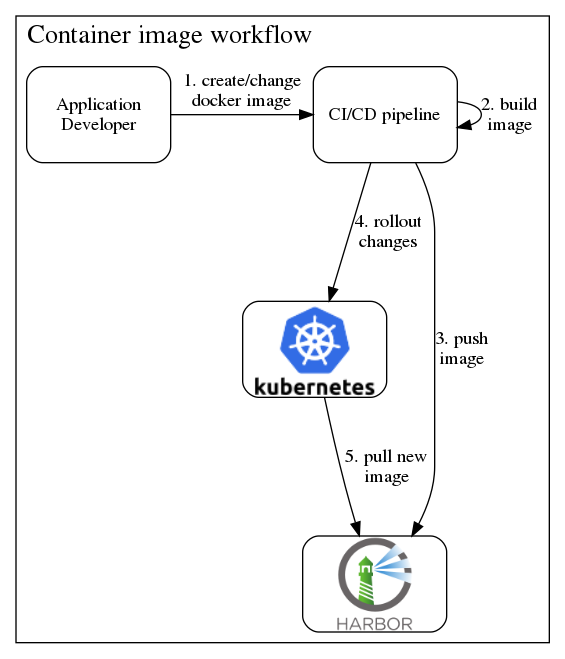
Container images will be pulled multiple times from the container registry. This is especially true in Kubernetes-based systems, because Pods are considered ephemeral and because the security-conscious default value for the imagePullPolicy is “always”. So any new start of a container will verify that the container image is the freshest possible, by connecting to the container registry.
There are many popular public container registries available as services, e.g. Docker Hub, Quay.io, and Google Container Registry. In contrast to those, Harbor is an open source software that you can self-host, or get as part of a Kubernetes-based platform.
Download the open source Kubernetes distribution.
All security features pre-configured from day one with Elastisys Compliant Kubernetes. Including RBAC, monitoring, logging, intrusion detection and more.
How to do Vulnerability Management via Image Scanning in Harbor
Harbor can be integrated with vulnerability scanners such as Trivy and Clair. Both of these provide comprehensive vulnerability detection at the OS package as well as language-specific package levels. That means that they can scan the entire container image, layer by layer, and investigate all the software that is present there.
They then pull information about known vulnerabilities from central databases, and present the results in an easy to understand way.
In Harbor, the results from such a scan looks like this:
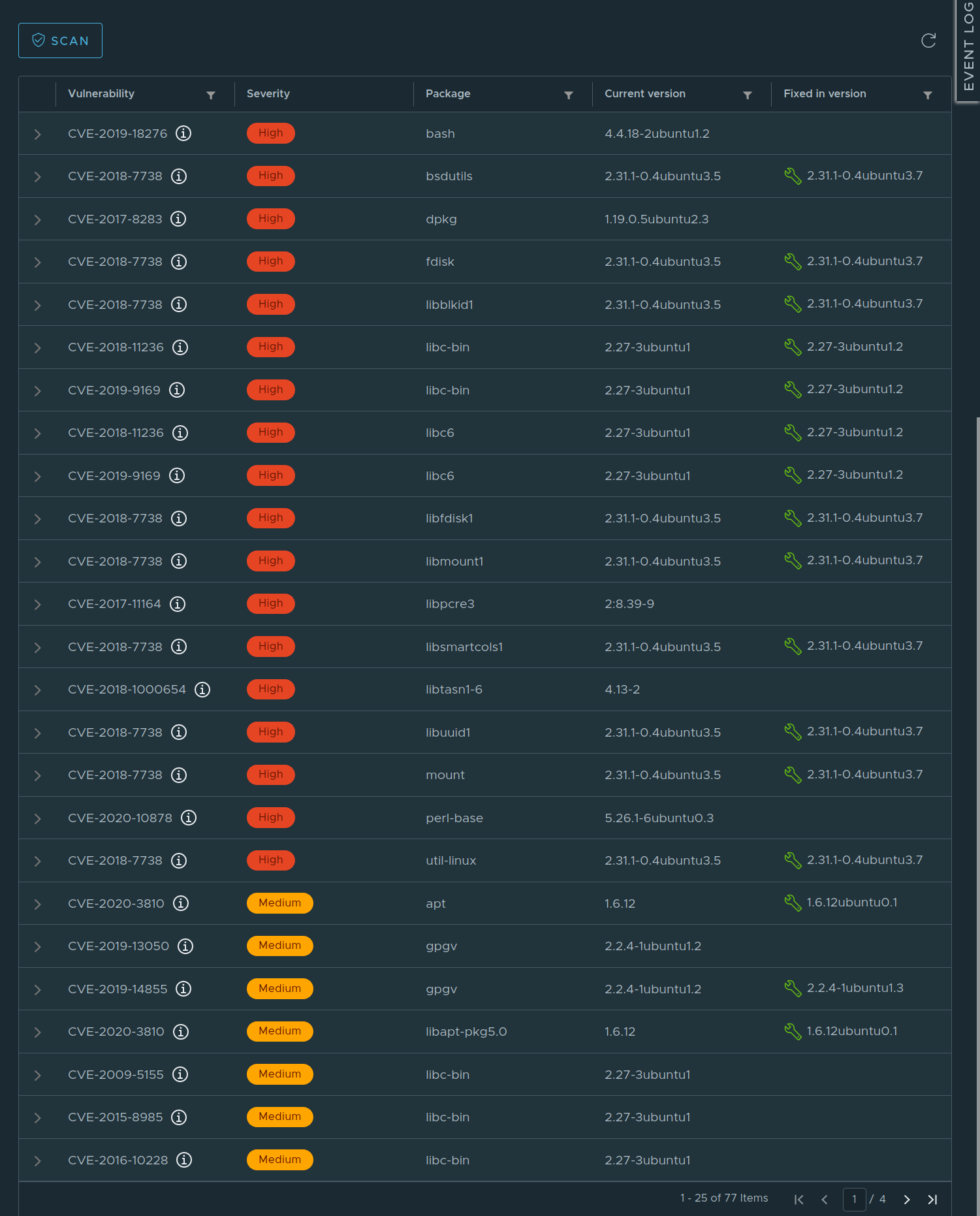
As you can see, the severity of each vulnerability is listed next to information about it.
In this way, Harbor and an integrated container image vulnerability scanner gives us the first two steps of vulnerability management: identification and evaluation.
But it also shows if a known fix is available to the vulnerabilities it has discovered. So we actually get parts of the third step (mitigation), too. It then becomes up to us to update our image and deploy it.
Harbor can further be configured to help in mitigation by setting a policy that will forbid it from serving images with known vulnerabilities. You can set the severity level, so that, for instance, only critical vulnerabilities will be prevented this way. You might be tempted to set it to any severity level, but you will then soon find that software today sadly comes with a lot of lower-level vulnerabilities. Most of those vulnerabilities are perhaps not relevant to your application at all (there is a research project for determining this automatically!).
Summary
Harbor, the open source container image registry, can be configured to help with the three steps of vulnerability management: identification, evaluation, and mitigation. Configured correctly, it can prevent application components with known vulnerabilities to be deployed to production, thereby reducing your attack surface considerably.

