In addition to offering a fully-managed Kubernetes platform as a service based on Welkin, Elastisys also offers DevOps consultancy services. With permission from our client, this blog post shows the work our DevOps engineers have implemented.
Key Benefits
Streamlined process
A streamlines process of audit preparation, supported by state of the art tools.
Documentation compilation
Support in compiling the InfoSec documentation necessary for the audit.
Evidence gathering
Assistance in gathering evidence showing how the requirements are fulfilled.
In the DACH region, the BSI IT-Grundschutz certification serves as a proof of trustworthiness, and is an information security requirement to offer work for the public sector. Elastisys has helped Data4Life, a German HealthTech company, prepare for their initial audit in 2022. In this case study, we share actionable advice and insights on how we built a streamlined process for passing the BSI IT-Grundschutz Audit.
Background
Companies in regulated industries, such as MedTech, HealthTech, and FinTech, as well as those processing personal data, need public trust to operate. In the DACH region (Germany, Austria and Switzerland), the IT-Grundschutz (formerly known in English as IT baseline protection) provided by Germany's Federal Office for Information Security (BSI) serves as such a proof of trustworthiness.
To obtain the IT-Grundschutz certificate, companies have to go through an audit process dealing with all aspects of IT security. Preparation for the audit requires a substantial amount of work on documenting the internal security policies and processes in line with the IT-Grundschutz requirements. In addition, it requires gathering evidence which clearly shows how these policies and processes are followed in practice. Both of these activities are strongly supported by a good process.
The Solution
In a recently completed project, Elastisys has supported Data4Life, the non-profit HealthTech company, during their preparation for the IT-Grundschutz audit. Our InfoSec engineers worked closely with the customer’s Information Security Officer (ISO) as well as experts from all the relevant customer’s departments in order to enable a timely delivery of high-quality IT security documentation required for the audit.

The tech stack
Our customer works in a commonly used environment a corporate wiki for their documentation and a ticketing tool for issue tracking and project management. For the duration of the project, we were given access to these customer’s systems, both the InfoSec documentation with the company's policies and procedures, as well as the technical specifications describing the implementation details of various systems used in the company.
Initial phase: How we established working group relations
At the beginning of the project we formed a working group with experts from all the relevant customer’s departments. In order to ensure good communication among the group members we mostly used a dedicated messaging tool and video calls.
During the initial phase of the project, we conducted video calls with experts from each department to learn about their area of expertise and responsibilities, as well as to get an overview of the IT systems they use, their way of working and experiences from the previous audits. This step was crucial to enable our InfoSec engineers to assign specific tasks to relevant customer’s departments at the later stages of the project.
Based on the documentation and initial video calls, we were able to:
- prepare an initial version of audit documentation, linking InfoSec and technical documentation with the IT-Grundschutz requirements,
- identify the gaps in the InfoSec documentation,
- suggest the type of evidence that should be gathered and included in the audit documentation.
Main phase: How we used the ticketing tool to streamline the audit preparation
Most of our work was performed on a dedicated ticket board, where each IT-Grundschutz requirement was represented as a separate ticket. Each ticket consists of:
- the actual IT-Grundschutz requirement text,
- the references to the relevant company’s policies and,
- the evidence showing how the requirement is fulfilled.
To be precise, for certain IT-Grundschutz modules, we created multiple issues for the same IT-Grundschutz requirement. That was the case for modules which were applicable to several IT systems and/or locations, such as module OPS.2.2 Cloud Usage - where the customer was using multiple SaaS products or INF.7 Office Workplace - where the customer uses offices in different geographical locations. Having separate tickets for each application of the IT-Grundschutz requirement enabled us to assign the issue to the relevant department and collect evidence specific for the particular application.
In order to streamline the audit preparation process we have developed a workflow with a Happy path and multiple Exception paths, describing the sequence of actions which should be taken by various actors while preparing the audit documentation. The workflow was further improved based on the feedback from the working group members.
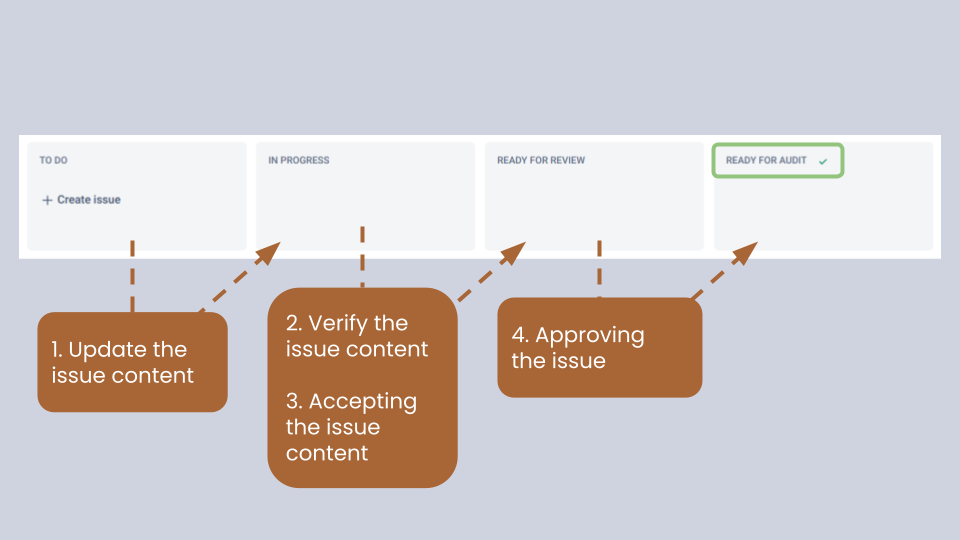
The usual path is depicted above.
In our issue ticket board, we have 4 columns for listing issues:
- TO DO - containing issues which are waiting for the initial processing by the Elastisys InfoSec engineer,
- IN PROGRESS - with issues that were already processed by the Elastisys InfoSec engineer are require feedback from the customer’s experts,
- READY FOR REVIEW - listing processed issues waiting for the approval of the ISO,
- READY FOR AUDIT - with fully processed and approved issues ready for the audit.
The following table summarises each step on the usual path:

In the first step, Updating the issue content, Elastisys InfoSec engineer prepares the audit documentation for the specific IT-Grundschutz requirement by making sure that the description is (1) up-to-date with the IT-Grundschutz Compendium, (2) the company’s internal policies are set according to the requirement and (3) links to relevant evidences are provided.
During the second step, Verifying the issue content, designated members of customer’s teams verify that the documentation prepared by the Elastisys InfoSec engineer reflects the actual policies and practises in-use at the company. Quite often, in this step, additional or more up-to-date evidence is provided by the customer's experts. Once the expert is satisfied with the issue, she adds a dedicated label to the issue, which indicates that the audit documentation is signed-off by the company’s representative.
The third step, Accepting the issue content, allows Elastisys InfoSec engineers to evaluate if the new information provided by the customer’s experts is relevant and if an adjustment in the Status indicating to what extent the IT-Grundschutz requirement is fulfilled is needed. For example thanks to some additional work and evidence provided the state might change from partially implemented to fully implemented.
Finally, in the fourth step, Approving the issue, the customer's ISO, who is ultimately responsible for the preparation for the audit, double-checks the whole audit documentation related to particular IT-Grundschutz requirement is complete.
Such a workflow enables parallel work by multiple Elastisys InfoSec engineers together with experts from multiple customer’s departments. This reduces bottlenecks and leads to a steady progress throughout all the IT-Grundschutz modules.
The Result
Having an appropriate tech stack and using it in the right way, as well as, a streamlined process, allowed us to prepare for the audit in a timely manner and reduce the overhead for the customer’s technical staff. Thanks to that, customer's experts could focus on providing suitable evidence of fulfilling BSI requirements and produce a high quality documentation for the audit. That led to a successful outcome of both the audit itself and the collaboration with the customer in general.
Recommendations for Passing the BSI IT-Grundschutz Audit
Based on our experiences we have also compiled a set of recommendations on how to streamline your IT-Grundschutz preparation process.
- Hold an initial meeting with persons involved in the audit preparation process, such as CISO, CTO, InfoSec engineers - set milestones and deadlines
- Define areas of responsibility of each department, so InfoSec engineers can assign tickets accordingly
- Designate at least two experts from each department
- Invite all the experts to the audit working group - use a commonly used means of communication, for example a dedicated messaging channel
- Agree on the workflow with all the persons involved, make adjustments if necessary
- Make sure that experts have enough time reserved for gathering evidences
- Evaluate the applicability of all the IT-Grundschutz module to your company as early as possible in order to avoid performing unnecessary work on modules which are irrelevant
- Create tickets for all applicable modules, decide in which cases multiple copies should be created to distinguish between different applications of the same IT-Grundschutz requirement
- Use "epics" to further structure the related issues so experts can easier understand the context of each requirement and process related issues in a single batch
- Track progress of the audit preparation - note number of issues in each column of the ticket board daily
- For Elastisys Kubernetes Platform as a Service customers, note that Elastisys Welkin is compliant with the “APP.4.4 Kubernetes modul”. This module was added in the 2022 edition of the BSI IT-Grundschutz.
- For companies that are not Elastisys Kubernetes Platform as a Service customers, please learn how we fulfil the requirements by visiting our website with the free Elastisys Welkin documentation.
